OSPF MD5 Auth Cracker
A python script to crack OSPF type 2 cryptographic authentication (MD5) secret keys from Wireshark capture files containing Hello Packets.
Skills I used for this project
- Researching and understanding a network protocol
- Packets analysis (with Wireshark)
- Parsing network capture files with Python
- Cryptography
How it works
Authenticated packets have a 'Auth Crypt Data' field containing a MD5 hash obtained by concatenating the OSPF packet's bytes with a secret key. Since all routers in the network know the secret key, they make their own hash and compare the two. If both match, that means the request is well authenticated. By doing this same process, we can bruteforce the secret key using wordlists.
The cracking part of this script is mostly a showcase/fun project. For optimal cracking performance/speed, I strongly recommend using John The Ripper.
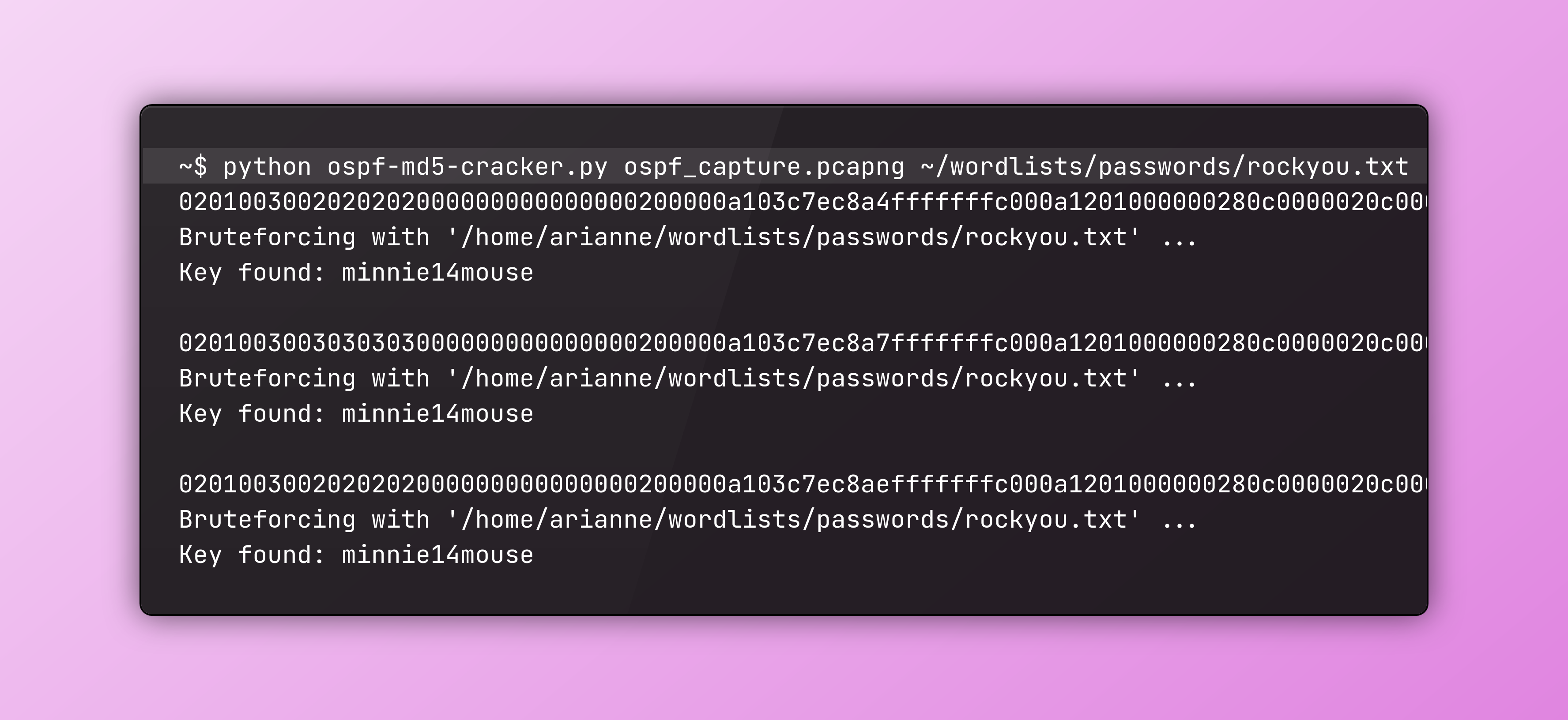
In action
Using a sample capture file: